Users offloaded to Wi-Fi
Keep the Control
Operators need to set policies to control and optionally charge offloaded users. With Enea Aptilo Wi-Fi SMP, it is possible to do so without back-hauling the traffic to the mobile core. Learn more about our Mobile Data Offloading solution.
Applying Policies from Mobile Core via Intelligent Lookups
It is possible – via our ServiceGlue functionality – to intelligently map different policy decisions implemented at the mobile operator to the corresponding parameters in the Wi-Fi network. Policy decisions can be looked up from any database at the mobile operator that supports SOAP/XML, LDAP, or RADIUS.
Policy decisions can include:
- Allowed locations for access
- Volume/time limitations
- Quality of Service (QoS)
- Prepaid or postpaid
- Type of user
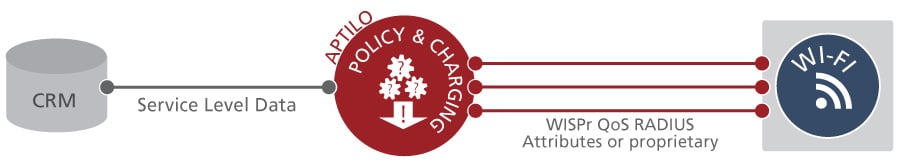
For instance, a subscriber’s service level data can be retrieved from the CRM system and mapped to Quality of Service (QoS) parameters in the Wi-Fi network. With Enea Aptilo SMP, the mobile operator can control the user experience even for locally offloaded traffic without having to backhaul traffic to the mobile core, which is a common scenario in the 3GPP architecture.
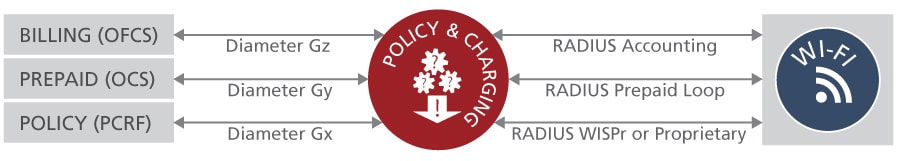
Applying Policies from the Mobile Core via Diameter Gx Interface
Mobile operators may have an existing PCRF for handling policy and charging decisions. These decisions are then communicated via the Diameter Gx interface to the packet gateway node (GGSN / P-GW / DPI nodes), which enforces the policies in the mobile network.
In Enea’s mobile data offloading solution, the policies from the PCRF are retrieved via the Diameter Gx interface and intelligently converted (via the Aptilo ServiceGlue mapping functionality) to the corresponding parameters in the Wi-Fi network to the extent of the capabilities of the specific Wi-Fi network.
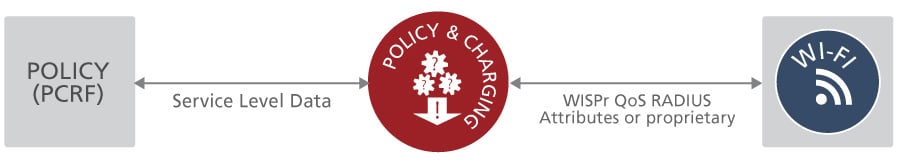
The same principles applies for the 5G architecture with the PCF function.
The policy converter in our solution is designed also to enable mapping and translation of policies to the specific attributes from vendors such as Aruba, Cisco and Ruckus utilizing their proprietary QoS control.
Examples of advanced QoS features are the Enea Aptilo SMP Automatic Bandwidth Balancer function where all available bandwidth is evenly distributed among active user sessions, or Aptilo Dynamic Bandwidth Throttling where a user gets a “bucket” of data and bandwidth is automatically and gradually throttled down as the “bucket” is consumed.
Applying policies from the Aptilo Service Management Platform
An alternative solution to the PCRF/PCF is to provision policies for the Wi-Fi sessions directly in the service management system for the Wi-Fi service. This have its merits as these systems typically understand Wi-Fi policies better than the standard PCRF/PCF. The Enea Aptilo SMP (software) and SMP-S (service on AWS), features a built-in Wi-Fi policy manager which has been proven in large-scale Wi-Fi deployments globally. Mobile operators can provision it with policies for the Wi-Fi users via one of our APIs or manually via GUI. It is also possible to combine this with the optional pre-integrated prepaid and captive portal functionality.